A Quick Guide to Using Clutch 2.0 to Decrypt iOS Apps
A few days ago someone told me that they weren’t able to install Crackulous on their jailbroken iOS device and asked if I could recommend an alternative they could use to decrypt iOS apps. Since Crackulous was a GUI frontend for Clutch I recommended that they check out Clutch but when I went to find a good tutorial I could only find ones showing older versions of Clutch instead of the newer Clutch 2.0 RC2. It’s not quite as friendly as the older versions of Clutch but it works like a champ on my jailbroken iPhone 5S running 8.1.2.
The easiest way to get Clutch 2.0 RC2 on your jailbroken device is to add the iPhoneCake repository to cydia using the URL http://cydia.iphonecake.com . Once that repository is added you should be able to install Clutch 2.0 as show in the image below.
Another option is downloading the sourcecode from the Clutch github repository at https://github.com/KJCracks/Clutch and compile it using Xcode with iOSOpenDev installed. Once Clutch2 was on my iOS device I used Putty to connect to it via SSH from my Windows system. I also could have used a terminal app on the iPhone itself and elevated my privileges to root.
Once I was connected I typed “Clutch2” which showed the following options:
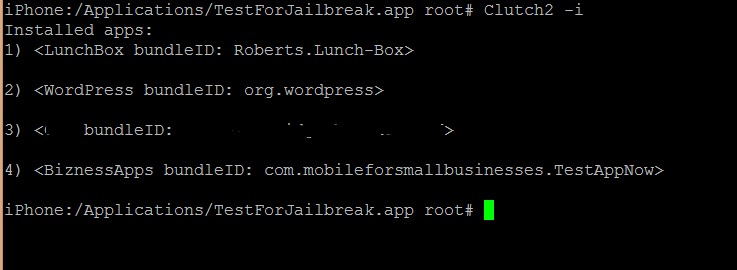
Typing “Clutch2 –i” displayed all of the app store apps installed on the device:
I decided to dump the third application (which I don’t want to display since I didn’t write the app) so I ran “Clutch2 –b <BundleID#>”. If I had wanted to dump the second app (WordPress) I would have typed “Clutch2 –b org.wordpress”. Clutch2 quickly generated the following output:
The decrypted binary was placed under the /var/tmp/clutch directory. I used ifunbox to copy both the decrypted binary and the original binary (located in /var/mobile/Containers/Bundle/Application/xxxx) to my computer so I could compare the before and after results. Normally Mach-O executable files contain code for multiple arm architectures and you need to use the OSX command line tool “lipo” to extract the arm version that you would like to analyze but in this case the application only contained code for armv7 so that wasn’t necessary.
Below you can see where I ran file on an iOS app with multiple architectures (armv7s and armv7) and file on this application which only has one architecture.
Once I confirmed that I wasn’t dealing with multiple architectures I used the strings command to extract the txt from both the original binary and the binary which Clutch2 produced. The original encrypted version is on the left and the post Clutch2 decrypted version is on the right.
As you can see the decrypted version gives us quite a bit more information about what’s going on inside of the application and I can start to use the tricks I learned in the SANS SEC575 course to analyze the app and it’s behavior.






Comments
Post a Comment